School art folder infected, files held for ‘ransom’
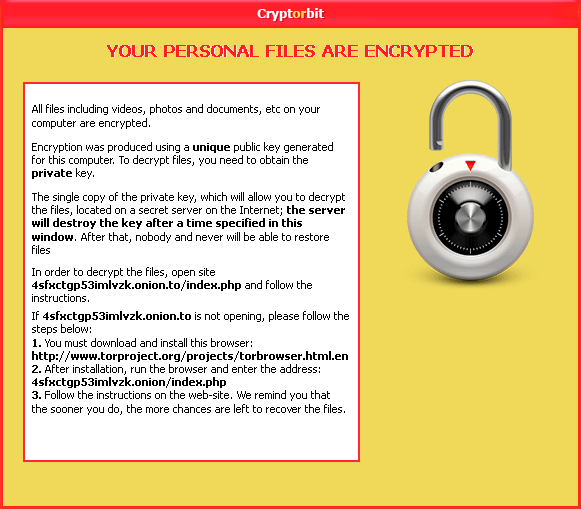
Photo Credit: The Glen Echo
This image, reputedly from the hacking group Cryptorbit, demands a ransom to retrieve encrypted files. Luckily for GRHS, that won’t be necessary.
February 25, 2014
The graphics folder—the cloud storage location for High School student images—has been held for ransom. Our school has been asked to pay half of a Bitcoin, which is roughly $600, to ensure the safe return of these files. Based on a document saved into the graphics folders, the school was informed that if the money is not paid, all of these files will be deleted.
Luckily for our art department, our technology department backs up all files on the drive each night. According to Mr. Kroft, “They are restoring [it] now from what was saved Monday night.” This means that by tomorrow, everything that was saved before 11:00 pm last night will be back to normal.
According to sources, a teacher accidentally opened a file that was infected with a virus, and last night, at approximately 12:45 am, the virus was unleashed on the system. That virus then spread across the entire Graphic Zeus drive.
Those who have tried to access the file are greeted with a message informing them that the files have been encrypted, and that if instructions are not followed and the ransom is not paid, all files will be deleted and nobody will be able to restore them. This type of infection is known as ‘ransomware.’
“We couldn’t do any work in media arts today because we had no access,” explained senior Anna Lis.
Most computers, which do not have back-up servers, would not have been able to restore these files, so a word of warning to individuals to beware of the files they open.
A previous version of this article errantly reported that a teacher had opened the file at 12:45 am. In actuality, the file was opened previously but the virus activated during the night.


